The software supply chain includes all the tools, codes, and third-party components used to build software. Just like a factory needs safe materials, software must have secure and trusted resources.
- What is Software Supply Chain?
- How It Differs from a Traditional Supply Chain
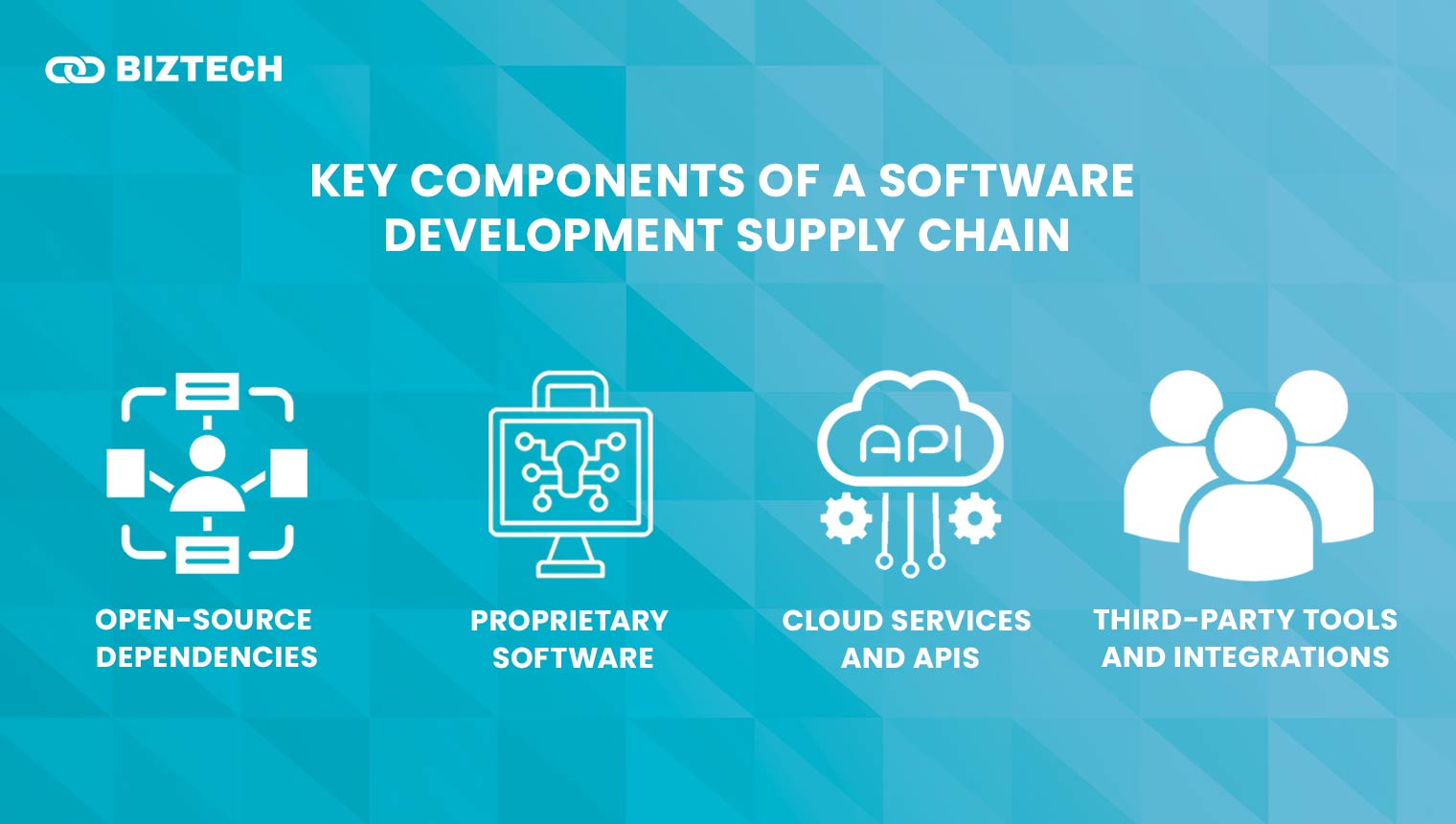
- Key Components of a Software Development Supply Chain
- 1. Open-Source Dependencies
- 2. Proprietary Software
- 3. Cloud Services and APIs
- 4. Third-Party Tools and Integrations
- The Role of Software Supply Chain in Secure Development
- How Secure Software Supply Chain Management Impacts Development Lifecycle
- Ensuring Code Integrity and Compliance
- Reducing Risks Associated with Third-Party Software
- Case Studies of Software Supply Chain Failures and Their Consequences
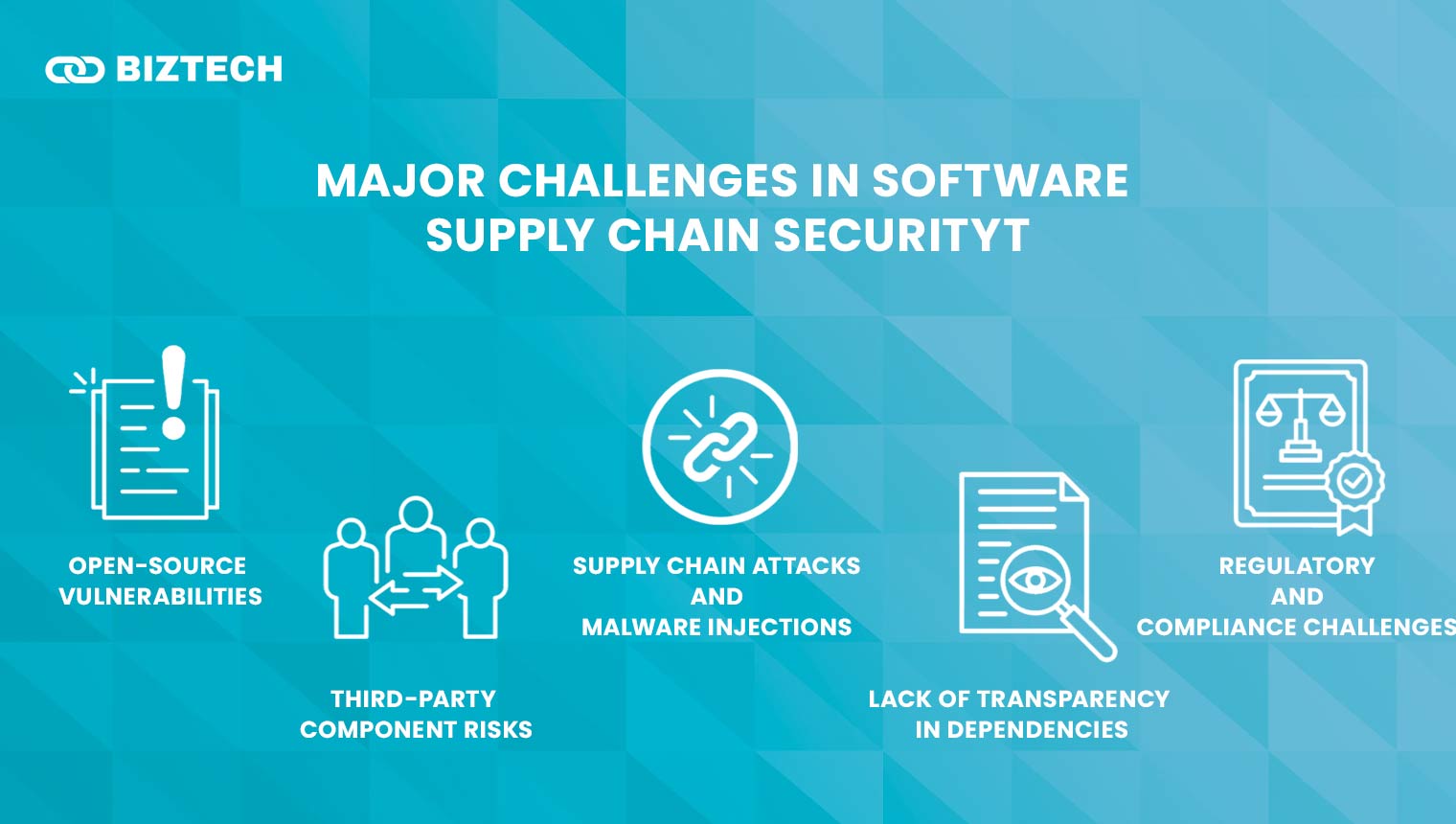
- Major Challenges in Software Supply Chain Security
- 1. Open-Source Vulnerabilities
- 2. Third-Party Component Risks
- 3. Supply Chain Attacks and Malware Injections
- 4. Lack of Transparency in Dependencies
- 5. Regulatory and Compliance Challenges
- Best Practices for Securing the Software Supply Chain
- Implementing Software Supply Chain Management
- Using Supply Chain Software Tools
- Following Secure Coding Practices
- Conducting Regular Security Audits and Vulnerability Assessments
- Integrating DevSecOps for Security
- Emerging Technologies and Trends in Software Supply Chain
- The Impact of AI and Automation in Software Supply Chain Management
- Blockchain for Software Provenance and Integrity
- The Future of Supply Chain Software in Ensuring Cybersecurity
- The Role of Zero-Trust Architecture in Securing the Software Supply Chain
- How Businesses Can Strengthen Their Software Supply Chain
- Conducting Vendor Risk Assessments
- Leveraging SBOM (Software Bill of Materials) for Transparency
- Building a Culture of Security Within Development Teams
- Case Study: How Top Tech Companies Secure Their Software Supply Chain
- Conclusion
Security is important because hackers can target weak points, insert malware, or steal data. A single compromised component can put an entire system at risk.
To stay safe, businesses must carefully manage their software supply chain. Regular security checks, updates, and best practices help prevent cyber threats.
Software supply chain management ensures software remains secure and reliable. In this blog post, we’ll explore its importance and how to strengthen it.
What is Software Supply Chain?
The software supply chain is the process of developing software using different tools, codes, and services. It includes everything developers use, from open-source libraries to cloud services.
You can take it as just like a factory that needs raw materials to make a product. Software companies require safe and reliable digital resources. If only one part of the chain is weak, it can cause many security problems.
How It Differs from a Traditional Supply Chain
A traditional supply chain moves physical products from one place to another. In contrast, a software supply chain moves digital components.
Instead of raw materials, it involves code, third-party tools, and cloud services. While physical supply chains face issues like delayed shipments, software supply chains face cyber threats and security risks.
Key Components of a Software Development Supply Chain
1. Open-Source Dependencies
Developers use free, open-source code to speed up software creation. However, if these codes have security flaws, hackers can exploit them.
2. Proprietary Software
Some companies use paid software that is privately owned. It offers better security but still needs regular updates to stay safe.
3. Cloud Services and APIs
Many applications rely on cloud storage and APIs (API is a tool that helps different software programs to work together). If these services get hacked, the whole system can be at risk.
4. Third-Party Tools and Integrations
Developers often use extra tools to add features to software. While helpful, these tools can introduce security gaps if not managed properly.
The Role of Software Supply Chain in Secure Development
A strong software supply chain is essential for building safe and reliable software. It helps developers create secure applications while protecting against cyber threats.
Hackers can insert malware, steal data, or disrupt systems without proper security. That’s why managing the software supply chain correctly is important for every business.
How Secure Software Supply Chain Management Impacts Development Lifecycle
Good software supply chain management ensures that only trusted tools and code are used in development. Developers check and update software regularly to keep it safe.
Security is added at every step of development, from implementing then coding to launching the full-fledged final product. This process reduces errors, prevents cyberattacks, and makes software more reliable.
Ensuring Code Integrity and Compliance
Developers must ensure the code is safe to use and follows the industry rules and regulations. This means checking for hidden security risks, keeping software updated, and following guidelines like ISO and NIST.
Secure software supply chain management ensures that every part of the code is tested and verified before being used.
Reducing Risks Associated with Third-Party Software
Most software depends on third-party tools, plugins, and cloud services. While these tools make development easier, they can also introduce security risks.
Hackers often target weak third-party software to break into systems. Companies must carefully choose reliable vendors, update software regularly, and monitor for threats.
Case Studies of Software Supply Chain Failures and Their Consequences
- SolarWinds Attack (2020): Hackers injected malware into software updates, and it affected thousands of businesses. It also includes governmental organizations. This attack showed the dangers of weak supply chain security.
- Log4j Vulnerability (2021): A security flaw in a popular open-source tool exposed millions of devices to cyber threats. Many companies struggled to fix the issue quickly.
- Codecov Breach (2021): Attackers modified a tool used by developers, stealing sensitive data from thousands of organizations. This case proved the need for strict security checks on third-party software.
A secure software supply chain protects businesses from these risks. By following best practices, companies can build safe, reliable, and ready software for the future.
Major Challenges in Software Supply Chain Security
The software supply chain faces many security risks that can lead to serious business problems. Cybercriminals target weak spots in software components, making security a primary concern.
Here are some key challenges:
1. Open-Source Vulnerabilities
Many software products rely on open-source components, which can have security flaws. Hackers often exploit these weaknesses if they are not updated regularly.
Since open-source code is widely shared, one vulnerability can affect many systems.
2. Third-Party Component Risks
Businesses use third-party software to save time, but these tools can introduce hidden risks. If a vendor does not follow strict security rules, attackers can use their software to enter a company’s system.
Companies must carefully check all third-party tools before using them.
3. Supply Chain Attacks and Malware Injections
Hackers sometimes inject malicious code into software during development or updates. This is referred to as a supply chain attack.
Once it’s installed, infected software has the potential to steal data or cause system damage. These attacks can spread quickly, affecting many users.
4. Lack of Transparency in Dependencies
Many software products have hidden dependencies, meaning they rely on other software components that may not be secure. Without a clear Software Bill of Materials (SBOM), businesses may not know what is inside their software, making it hard to fix security issues.
5. Regulatory and Compliance Challenges
Governments and industries now require businesses to follow strict security rules. Keeping up with these regulations can be difficult, especially for companies that work with multiple vendors.
Non-compliance can lead to fines, legal issues, and reputational damage.
Best Practices for Securing the Software Supply Chain
Keeping the software supply chain secure is essential to prevent cyber threats. All businesses must follow best practice guidelines to defend their software programs from vulnerabilities.
Following are some key steps to improve software security:
Implementing Software Supply Chain Management
Strong software supply chain management helps businesses track and secure every part of their software. This includes monitoring suppliers, checking for security risks, and ensuring that all software components are safe before use.
Using Supply Chain Software Tools
Security tools help businesses detect and fix problems in their software supply chain. These tools:
- Scan software for vulnerabilities.
- Monitor third-party components for security issues.
- Alert teams if there are signs of a cyberattack.
Using automation and AI-powered security tools can make monitoring more effective.
Following Secure Coding Practices
Software developers must follow secure coding instructions to reduce risks. Best practices include:
- Writing clean and tested code.
- Avoiding hardcoded passwords and sensitive data.
- Using encryption to protect user information.
Secure coding helps prevent common attacks like malware injections.
Conducting Regular Security Audits and Vulnerability Assessments
Businesses should conduct daily security checks on their software. So conducting daily security checks, audits, and vulnerability assessments can help:
- You can identify outdated or weak components.
- Try to fix security issues before hackers can exploit them.
- You can also ensure compliance with security regulations.
Most importantly, frequent security checks keep the software supply chain strong and reliable.
Integrating DevSecOps for Security
DevSecOps (Development, Security, and Operations) makes sure that security is implemented throughout the software development process. It helps teams:
- Detect and fix vulnerabilities early.
- Automate security testing in development.
- Create a culture of security awareness.
By using DevSecOps, businesses can build secure software from the start instead of fixing issues later.
Emerging Technologies and Trends in Software Supply Chain
The software supply chain is constantly improving as new technologies emerge. Companies must stay ahead of cyber threats by implementing advanced tools and strategies.
Let us look at the latest trends influencing the future of software supply chain security.
The Impact of AI and Automation in Software Supply Chain Management
AI and automation are changing software supply chain management by increasing security and efficiency. AI-powered tools can:
- Detect vulnerabilities faster by analyzing large amounts of data.
- Automate security patches and updates to reduce risks.
- Identify suspicious activities in real time, preventing cyberattacks.
Automation also helps reduce human errors, which are a common cause of security breaches.
Blockchain for Software Provenance and Integrity
Blockchain technology ensures software integrity by maintaining a transparent and tamper-proof record of all elements used during the development of software. It helps in:
- Tracking the origin of software components to prevent counterfeit code.
- Ensuring that updates come from trusted sources.
- Enhancing security in software licensing and distribution.
The Future of Supply Chain Software in Ensuring Cybersecurity
Supply chain software is becoming more advanced to protect against cyber threats. Future trends include:
- AI-driven risk assessment: Identifying security gaps before they become major threats.
- Cloud-native security solutions: Protecting software that runs in cloud environments.
- Automated compliance tools: Ensuring that all components meet security standards.
The Role of Zero-Trust Architecture in Securing the Software Supply Chain
The zero-trust model holds that no user, device, or application is automatically trustworthy. It requires strict verification at every step. Key principles include:
- Least privilege access: Where users are given the permissions only they require.
- Continuous monitoring: Every action is tracked to detect suspicious behavior.
- Multi-factor authentication (MFA): Adding extra security layers to prevent unauthorized access.
Zero-trust security helps protect the software supply chain from insider threats, malware, and supply chain attacks.
How Businesses Can Strengthen Their Software Supply Chain
Securing the software supply chain requires more than just having the right tools; it also necessitates a strategic approach. Companies must assess risks, improve transparency, and build a security-first culture.
Here’s how businesses can strengthen their software supply chain and reduce vulnerabilities.
Conducting Vendor Risk Assessments
Third-party vendors play an important role in software development by introducing risks related to security. Businesses should:
- Evaluate vendors’ security policies before integrating their software.
- Require vendors to follow strict security standards.
- Regularly audit third-party software for vulnerabilities.
Companies can reduce the risks associated with using compromised software by carefully selecting vendor partners.
Leveraging SBOM (Software Bill of Materials) for Transparency
A Software Bill of Materials (SBOM) is a complete listing of all components present in a software product. It helps businesses:
- Identify potential security risks in dependencies.
- Ensure that all software components are updated and verified.
- Improve compliance with security regulations.
Building a Culture of Security Within Development Teams
Security should be a shared responsibility with all teams, not just the IT department. To build a strong security culture, companies should:
- Train new developers on secure coding practices.
- Encourage developers to perform security testing at every stage of development.
- Reward teams for identifying and fixing vulnerabilities early.
A proactive approach to security helps prevent cyberattacks before they happen.
Case Study: How Top Tech Companies Secure Their Software Supply Chain
Leading tech companies use advanced security strategies for securing their software supply chains. For example:
- Google uses AI-driven security monitoring to detect threats in open-source software.
- Microsoft enforces a strict zero-trust model to protect its supply chain.
- Apple verifies all third-party applications through a secure review process before they reach users.
Conclusion
Securing the software supply chain is crucial because cyber threats are increasing daily. Businesses must take smart steps to keep their software safe and follow security rules.
This includes checking vendor risks, using SBOMs to visualize all software parts, and prioritizing security. New technologies, such as AI, blockchain, and zero-trust security, are helping make software more secure.
Implementing all the tools and strategies explained above can help companies stop cyberattacks, protect their users, and develop secure software. Focusing on security today will help businesses stay safe and trusted in the future.