Your smart devices make life easier, but they also come with risks. Cybercriminals can target your connected devices, from smart TVs to security cameras, stealing data or even taking control. This leaves your personal information exposed and open to attacks. You risk losing your privacy, money, and safety without proper security.
- IoT Cybersecurity: Definition and Importance
- Components of Your IoT (Internet of Things)
- Your IoT (Internet of Things) is Not Fully Safe
- Common Threats to Your IoT
- Device Hijacking
- Data Interception
- Man-in-the-Middle Attacks
- Malware & Ransomware
- Denial-of-Service (DoS)
- Insecure APIs
- Weak Passwords
- Lack of Updates
- Physical Tampering
- 5 Ways IoT Cybersecurity Eliminates (or Prevents) These Threats
- 1. Strong Encryption
- 2. Regular Software Updates & Patch Management
- 3. Strong Authentication Methods
- 4. Network Segmentation
- 5. Secure APIs and Device Interfaces
- Simple Practices You Can Do To Enhance Your IoT Cybersecurity
- Change Default Passwords
- Disable Unnecessary Features
- Use a Guest Network for IoT Devices
- Limit IoT Device Connectivity
- Monitor Your IoT Devices Regularly
- Frequently Asked Questions (FAQs)
But there’s a way to protect yourself. IoT cybersecurity helps keep your devices safe from threats. It protects your data and blocks cyberattacks before they happen.
IoT Cybersecurity: Definition and Importance

IoT cybersecurity protects internet-connected devices like smart homes, industrial tools, and healthcare systems from cyber threats. It is important because a single hack can crash the network and give a hacker full control of the system.
Cybersecurity is important for the Internet of Things (IoT) because many devices we use, like smart thermostats or fitness trackers, are connected to the internet.
These devices collect and share personal information. Hackers can break into these devices, steal data, or even control them if not properly protected.
Strong cybersecurity helps keep our devices and personal information safe from such threats.
This risk is incredibly high in defense and military operations, where IoT devices store highly sensitive information. A weak network point or an unprotected device can allow hackers to access critical intelligence or even cause physical damage to the entire network.
The risks have increased with governments, healthcare systems, and businesses’ dependence on IoT for connectivity and efficiency.
Each new device connected to a network adds another entry point for hackers. In the wrong hands, stolen data can lead to severe damage, especially in defense logistics or national security.
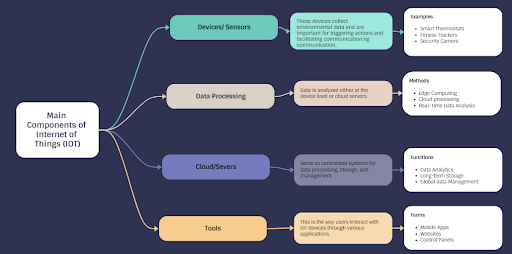
Components of Your IoT (Internet of Things)
Knowing its main components is important to fully understand the Internet of Things (IoT). Each component has a unique role in making IoT devices function properly. Here’s a breakdown:
1. Devices/Sensors
These are the “things” in IoT. Devices and sensors gather environmental information, such as temperature, motion, humidity, and light.
Smart thermostats, fitness trackers, and security cameras are examples of such devices. The data they gather is essential for triggering actions or sending information to other devices or systems.
2. Connectivity
This component connects devices to the internet. Connectivity allows devices to send and receive data and enables real-time communication with remote control.
For example, connectivity could be done using Wi-Fi, networks, Bluetooth, or other protocols.
3. Data Processing/Edge Computing
When gathered in one place, data frequently needs to be processed. Data processing happens at the device level (edge computing) or through a cloud server. This is where the information gets analyzed, and decisions are made.
For example, a smart thermostat might adjust room temperature based on real-time data about your home’s climate.
4. Cloud/Servers
Most data processing and storage happen in the cloud or on servers. Data is transferred to centralized systems for in-depth analysis or long-term storage, enabling large-scale data management, analytics, and insights.
For example, cloud systems can store data from thousands of IoT devices across the globe.
5. User Interface/Applications
This is how you interact with IoT devices. It can be a mobile app, website, or control panel that lets you manage and monitor your devices.
The user interface is how you control the IoT ecosystem, whether adjusting a smart home system, reviewing your fitness data, or maintaining security cameras.
For example, user interfaces for IoT devices include mobile apps like Nest for controlling smart thermostats, Fitbit for tracking fitness data, and websites like Ring for managing security cameras. These apps and sites allow users to monitor and adjust settings for their connected devices, making interacting with IoT technology simple and convenient.
Your IoT (Internet of Things) is Not Fully Safe
Common Threats to Your IoT
| Threats | Description |
| Device Hijacking | Hackers gain unauthorized control over IoT devices, often for malicious purposes. |
| Data Interception | Sensitive data is intercepted while being transmitted between devices and networks. |
| Man-in-the-Middle Attacks | Attackers have the ability to read and change communications between IoT devices and servers. |
| Malware & Ransomware | Malicious software is installed on IoT devices to disrupt functionality or demand ransom. |
| Denial-of-Service (DoS) | Attackers overload devices or networks, making them unavailable to users. |
| Insecure APIs | Hackers can gain access to IoT systems or data by exploiting poorly secured APIs. |
| Weak Passwords | Passwords of IoT devices are easy to guess. |
| Lack of Updates | IoT devices that are not updated are open to hacking attacks. |
| Physical Tampering | Attackers manipulate physical devices to gain access to sensitive data or systems. |
Device Hijacking
Attackers gain control over IoT devices to use them for botnets, spying, or launching attacks on other systems. These hijacked devices can also be used for unauthorized actions.
Data Interception
Since many IoT devices transmit data wirelessly, hackers can intercept this information, especially if it’s not encrypted, leading to potential data theft or misuse.
Man-in-the-Middle Attacks
In this attack, the hacker intercepts communications between two devices, allowing them to read or edit messages being sent, which could cause misinformation or unauthorized access.
Malware & Ransomware
IoT devices can become infected with malicious software that disrupts normal operations or locks the device until a ransom is paid to the attacker.
Denial-of-Service (DoS)
By flooding IoT devices or networks with excessive traffic, attackers can cause a disruption, making the devices or services unavailable to legitimate users.
Insecure APIs
Many IoT devices depend on APIs to connect with other services. If APIs are not properly secured, they become open to hacking attacks that could reveal sensitive data or take control of the devices.
Weak Passwords
Most of the IoT devices have default or weak passwords that hackers can easily guess. It allows them to gain unauthorized access to the device and its data.
Lack of Updates
Outdated devices frequently lack critical security patches, making them easy targets for hackers who misuse known errors.
Physical Tampering
Hackers can physically tamper with IoT devices to steal information directly from them or bypass security measures to gain network access.
5 Ways IoT Cybersecurity Eliminates (or Prevents) These Threats
1. Strong Encryption
Strong encryption involves converting data into a secure format that prevents unauthorized individuals from accessing it.
IoT devices can use encryption to protect data transmitted across networks, making it unreadable to hackers. To implement it, ensure all communications between IoT devices and their servers are encrypted with strong encryption algorithms such as AES.
Threats Prevented:
- Data Interception
- Man-in-the-Middle Attacks
- Device Hijacking
2. Regular Software Updates & Patch Management
Software updates and patches address known errors and reduce the risk of being used by hackers.
Regular updates are required to ensure the security of IoT devices and systems. Implement automated updates or use a device management platform to update all devices consistently.
Threats Prevented:
- Lack of Updates
- Malware & Ransomware
- Device Hijacking
3. Strong Authentication Methods
Multi-factor authentication (MFA) is one of the best robust authentication methods.
MFA is a security process requiring users to provide two or more verification factors to gain access to an account or system. It increases security by combining something you know (password), something you have (mobile device), and something you are (fingerprint).
It provides an additional layer of security. Instead of just passwords, IoT devices and systems may request further verification, such as a code sent to your phone or a fingerprint scan. This makes unauthorized access much more challenging.
Threats Prevented:
- Weak Passwords
- Device Hijacking
- Insecure APIs
4. Network Segmentation
Network segmentation is dividing your network into smaller and specialized parts to prevent attacks from spreading.
For example, you can separate IoT devices from critical systems and the broader network. This restricts access to sensitive data, lowering the likelihood of large-scale breaches.
Threats Prevented:
- Denial-of-Service (DoS)
- Malware & Ransomware
- Physical Tampering
5. Secure APIs and Device Interfaces
Only approved users and services can access IoT devices through secure APIs and device interfaces.
Strong authentication, encryption, and secure coding practices for APIs prevent unauthorized access to IoT systems and the data they generate.
Threats Prevented:
- Insecure APIs
- Device Hijacking
- Data Interception
Simple Practices You Can Do To Enhance Your IoT Cybersecurity
Change Default Passwords
One of the simplest yet most effective ways to improve IoT security is by changing devices’ default passwords.
Many IoT devices, such as cameras or smart thermostats, come with publicly known default passwords that are easy to guess. Changing these to strong, unique passwords ensures unauthorized users cannot quickly gain access.
How to Implement:
- Check your IoT device’s user manual or settings for the default login information.
- Try to replace the default password with a strong one that uses a random combination of alphabetical letters, numbers, and symbols.
- Use a password manager to keep track of these passwords securely.
Disable Unnecessary Features
Many IoT devices, such as remote access or certain communication channels, have features you might never use. Disabling unnecessary features reduces the attack surface and limits how hackers can access your device.
How to Implement:
- Review your device’s settings and disable features like remote control, voice commands, or unused Wi-Fi networks.
- Turn off Bluetooth, GPS, or other services that aren’t needed for your device to function.
Use a Guest Network for IoT Devices
IoT devices can introduce security risks to your main home or office network. Place these devices on a separate guest network to prevent them from accessing sensitive data or other devices on your primary network.
How to Implement:
- Create a guest Wi-Fi network on your router just for IoT devices.
- Keep this network separate from your main devices and data storage.
- Ensure the guest network has a strong password and that it’s encrypted.
Limit IoT Device Connectivity
The fewer connections your IoT devices make, the less likely they are to be hacked. Limiting their connections to only what’s necessary helps reduce potential risks.
How to Implement:
- Avoid connecting devices to the internet when not needed.
- Disconnect devices from your network when they are not in use, especially if they can access sensitive data.
Monitor Your IoT Devices Regularly
Regularly checking your IoT devices for unusual activity helps you detect potential security threats early. This can include monitoring device status, checking for firmware updates, or reviewing connected devices.
How to Implement:
- Check the app or software associated with your IoT device for any alerts or updates.
- Check connected devices and permissions regularly to ensure that only trusted devices can access them.