Stay connected with BizTech Community—follow us on Instagram and Facebook for the latest news and reviews delivered straight to you.
The cybersecurity world has been shocked again by the emergence of a new malware threat called SparkCat, which targets explicitly cryptocurrency users on Android and iOS platforms. Based on the latest report from Kaspersky released on 4 February 2025, this malware has successfully infiltrated applications available in official application stores such as the Google Play Store and Apple App Store.
Evolution of Mobile Malware Threats
The malware threat to mobile devices has undergone significant evolution, particularly in the context of crypto significantly evolved of SparkCat. ESET research in March 2023 identified attacks that utilized messaging apps to steal crypto data. However, SparkCat takes this threat to a more dangerous level with its more advSparkCat’s more advanced technical capabilities takel capabilities.
SparkCat Characteristics and Deployment Methods
SparkCat shows a high level of sophistication in its distribution methods. The malware is hidden within legitimate-looking applications, using a malicious framework or SDK specifically designed to steal recovery seed phrases from users’ crypto wallets. Alarmingly, the malware has recorded over 242,000 downloads on the Google Play Store and is the first malware to successfully breach App Store security.
Working Mechanism on Android Platform
- Utilizes Google ML Kit with OCR plugin
- Able to recognize text in images in the device gallery
- Sends the found data to the command server (C2)
Working Mechanism on iOS Platform
- Uses more complex protocols
- Developed with Rust programming language
- Harder to detect by security systems
ComeCome Case: A Real Example of SparkCat Infiltration
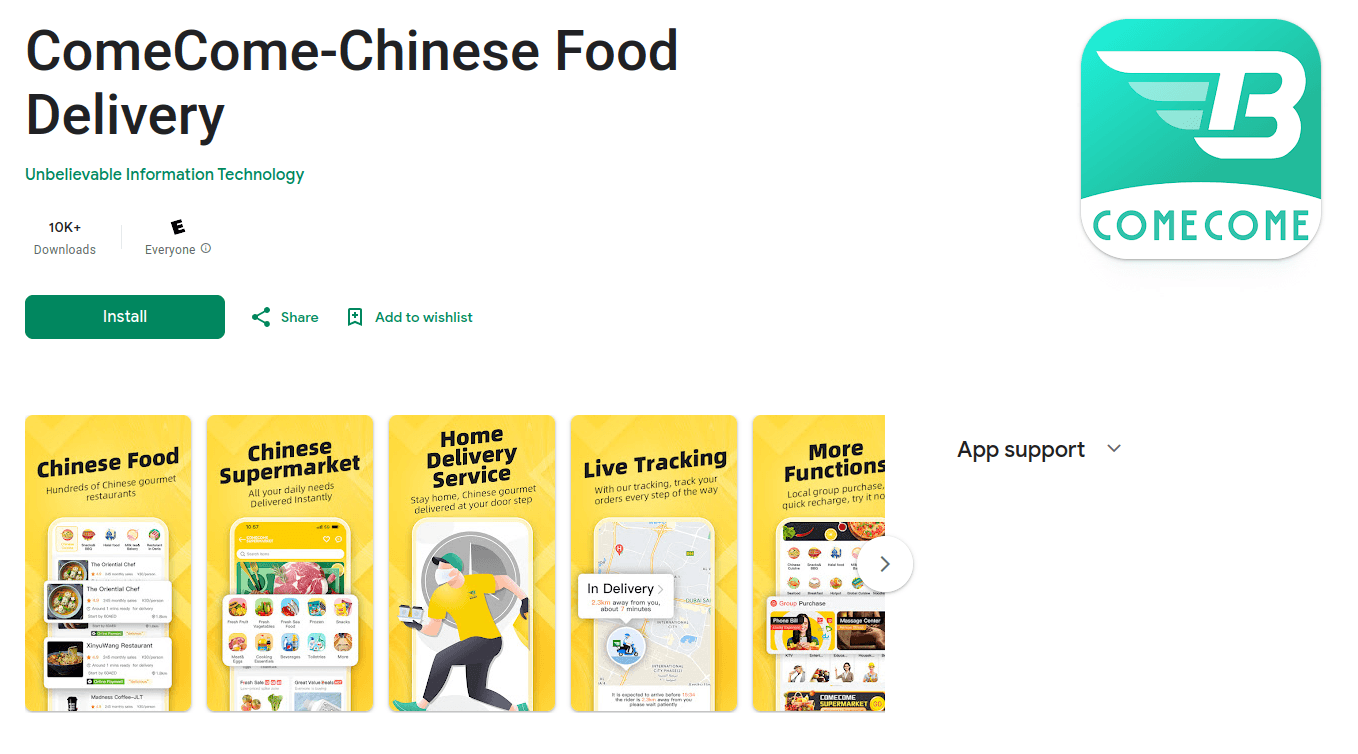
One of the most attention-grabbing cases is SparkCat’s infiltration into ComeCome, a popular food delivery app in the UAE and Indonesia. With over 10,000 downloads on the Google Play Store, this app is an example of how malware can infiltrate legitimate-looking apps.
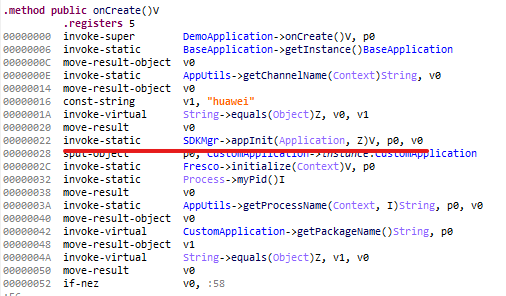
In version 2.0.0 of the ComeCome app, researchers found suspicious changes to the Application class, where there was initialization of a malicious SDK component named Spark. This process involves:
- Downloading an encrypted configuration file from the GitLab server
- Initiation of text recognition process in images
- Search for recovery seed phrase
- Transmission of encrypted data via TCP socket
Recovery Phrase Stealing Technique
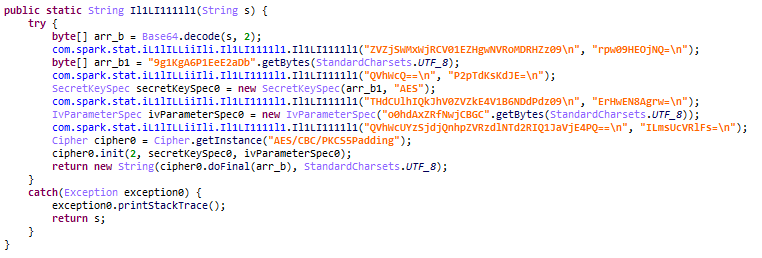
SparkCat uses a very sophisticated method to steal crypto recovery phrases. After gaining access permission to the gallery, the malware uses three main approaches:
- Keyword-based search in multiple languages
- Analysis of the number of words in the image
- Check using an encrypted local dictionary
The malware is capable of recognizing keywords in multiple languages, including Chinese, Japanese, Korean, and English, relating to recovery phrases or “mnemonics”.
Threat from Infected Apps
Further investigation revealed that SparkCat’s reach was much wider than previously thought. In addition to attacking the ComeCome food delivery app, the malware has infected various other unrelated apps. Worryingly, a number of these infected apps can still be accessed and downloaded through official app stores, making less vigilant users potential victims.
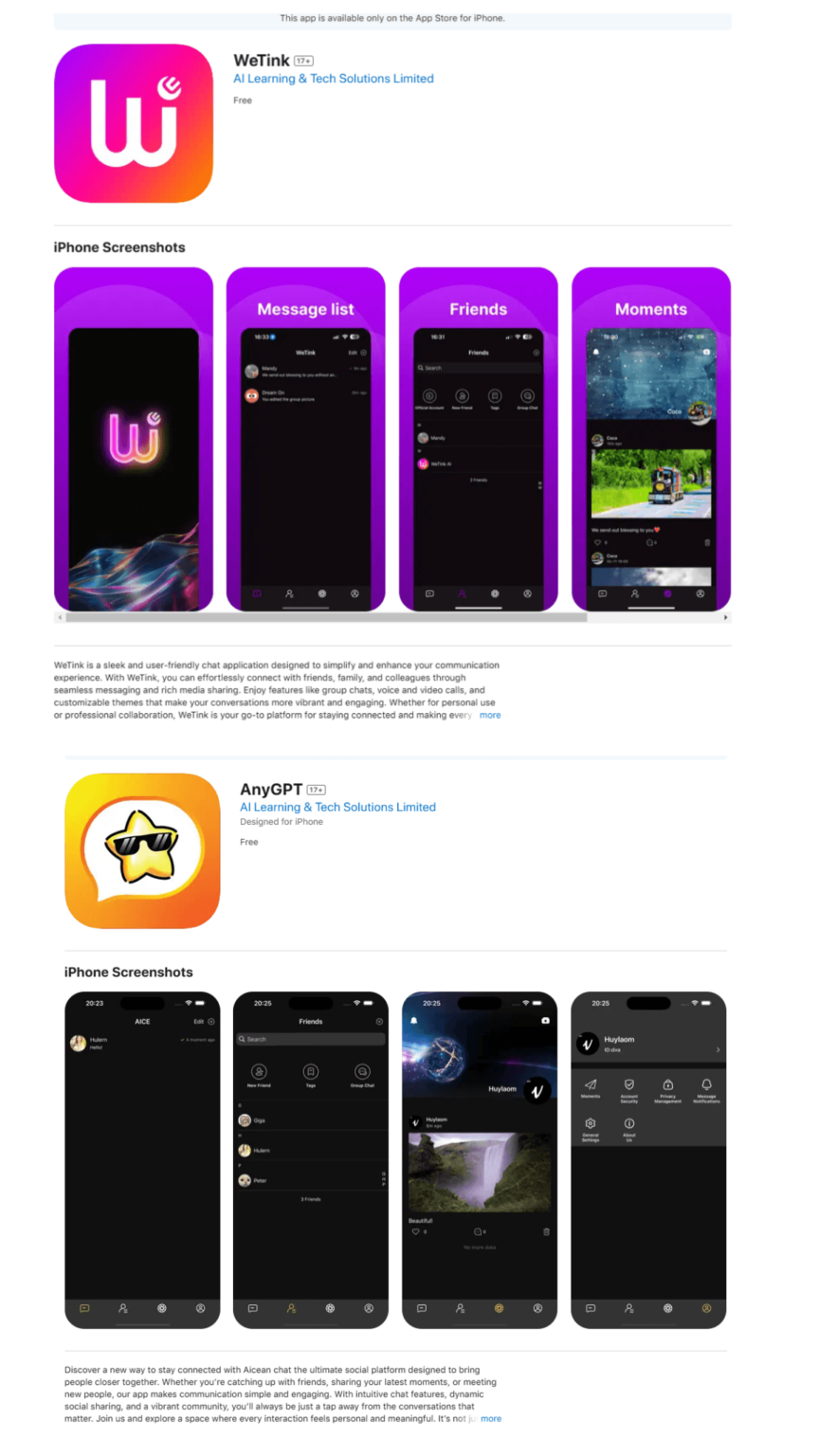
A more surprising finding was SparkCat’s success in penetrating the App Store’s security system. While the majority of infected apps came from unofficial sources, investigations confirmed that several apps on the App Store had been infiltrated by this malicious framework. Some of them were even intentionally made fake to trap users. This situation shows that even platforms known for having high security standards, like Apple, are not completely immune to the threat of sophisticated malware.
Implications and Preventive Measures
SparkCat’s discovery shows that even official app stores like the Google Play Store and App Store are not completely safe from malware infiltration. Some important implications to note:
Risks Faced
- Theft of personal data and sensitive information
- Unauthorized access to crypto wallets
- Potential for significant financial loss
Recommended Precautions
- Always carefully check the permissions requested by apps
- Be wary of apps that request irrelevant access
- Avoid storing recovery phrases in digital form
- Regularly update device security systems
- Use apps only from trusted sources
Conclusion
The emergence of SparkCat is an important reminder that cybersecurity threats continue to evolve, especially in the cryptocurrency industry. Users need to increase their vigilance and implement stricter security practices, especially in managing their digital assets. Although platforms such as the Google Play Store and App Store have strong security systems, they are not 100% safe from infiltration by sophisticated malware such as SparkCat.